Risk management is a comprehensive process that involves identifying potential threats to assets, evaluating these threats in relation to asset value and countermeasure costs, and implementing cost-effective solutions to mitigate or reduce risks. This process is crucial for developing and implementing information security strategies that align with an organization’s mission.
The primary objective of risk management is to reduce risk to an acceptable level, which varies depending on the organization’s specific circumstances, including asset value, budget constraints, and other factors. It’s important to note that while a completely risk-free environment is unattainable, significant risk reduction is often achievable with modest effort.
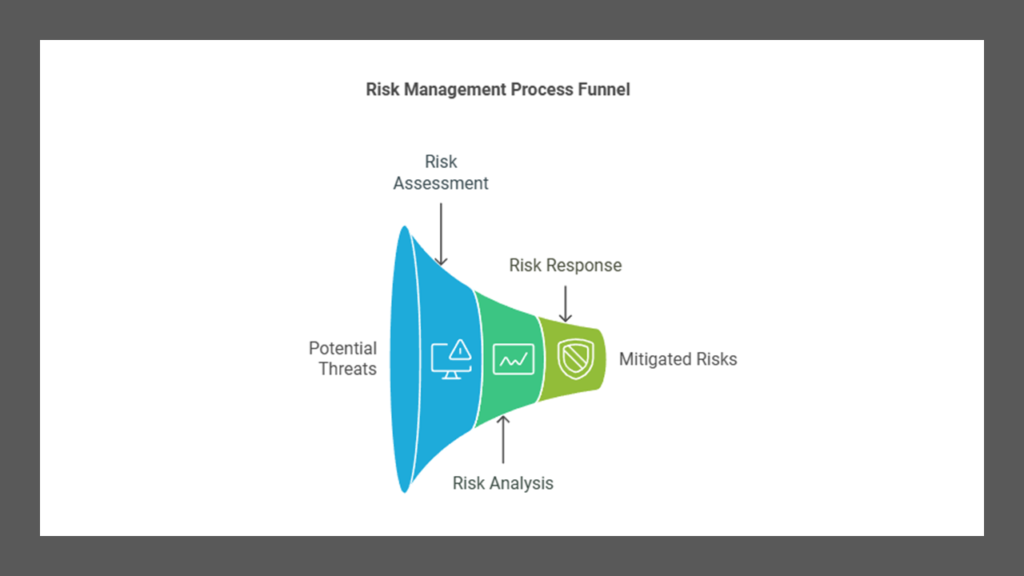
Risk management consists of two main components:
- Risk assessment/analysis: This involves examining the environment for risks, evaluating threat events based on likelihood and potential damage, and assessing the cost of various countermeasures.
- Risk response: This includes evaluating countermeasures using cost/benefit analysis, adjusting findings based on various factors, and proposing response options to senior management.
A related concept is risk awareness, which focuses on increasing knowledge of risks within an organization. This includes understanding asset values, identifying existing threats, and recognizing the responses implemented to address identified risks.
Risk Terminology and Concepts
Understanding the terminology used in risk management is crucial:
- Asset: Anything used in a business process or task, whether tangible or intangible.
- Asset Valuation: The process of assigning value to an asset based on various factors.
- Threats: Potential occurrences that may cause undesirable outcomes for an organization or asset.
- Threat Agents/Actors: Entities that intentionally exploit vulnerabilities.
- Vulnerability: A weakness in an asset or absence of a safeguard.
- Exposure: Susceptibility to asset loss due to a threat.
- Risk: The likelihood that a threat will exploit a vulnerability to cause harm.
- Safeguards: Mechanisms that reduce vulnerabilities or protect against threats.
- Attack: Intentional exploitation of a vulnerability by a threat agent.
- Breach: Successful bypassing of a security mechanism.
Risk Calculation
Risk can be conceptually expressed as:
Risk = Threat×VulnerabilityRisk=Threat×Vulnerability
Or
Risk=Probability of Harm×Severity of HarmRisk=Probability of Harm×Severity of Harm
This formula emphasizes that risk increases with both the likelihood of a threat occurring and the potential damage it could cause.
Asset Valuation
Asset valuation is a critical step in risk analysis. It involves assigning a specific dollar value to an asset, considering both tangible and intangible factors. This valuation guides the level of safeguards deployed to protect the asset. The general rule is that annual safeguard costs should not exceed the potential annual cost of asset value loss.
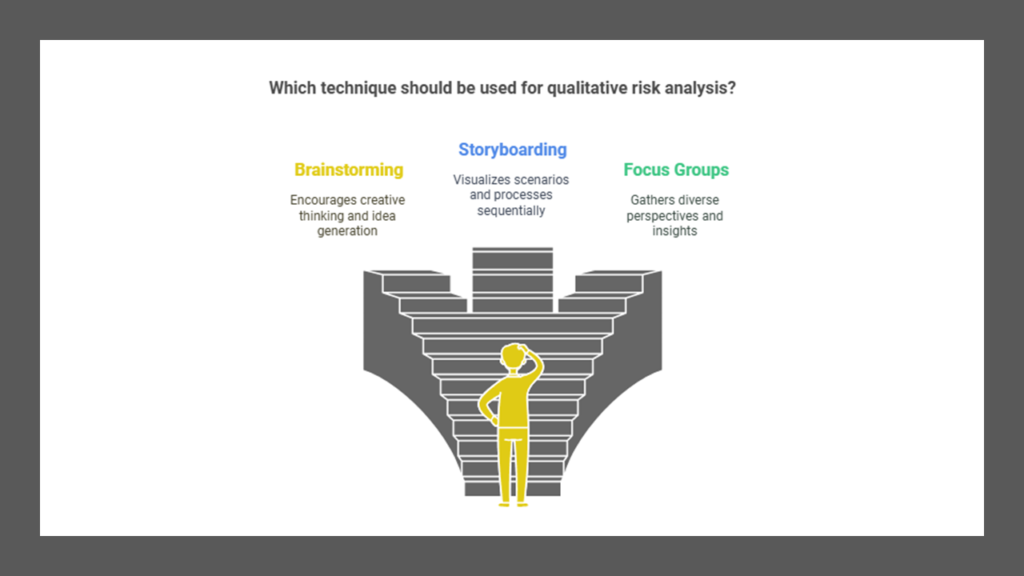
Qualitative Risk Analysis
Qualitative risk analysis is based on scenarios, perceptions, and intuitive judgments rather than precise mathematical calculations. It involves ranking threats on a relative scale to evaluate risks, costs, and effects. Techniques for qualitative risk analysis include:
- Brainstorming
- Storyboarding
- Focus groups
- Surveys and questionnaires
- Scenarios
- Delphi technique
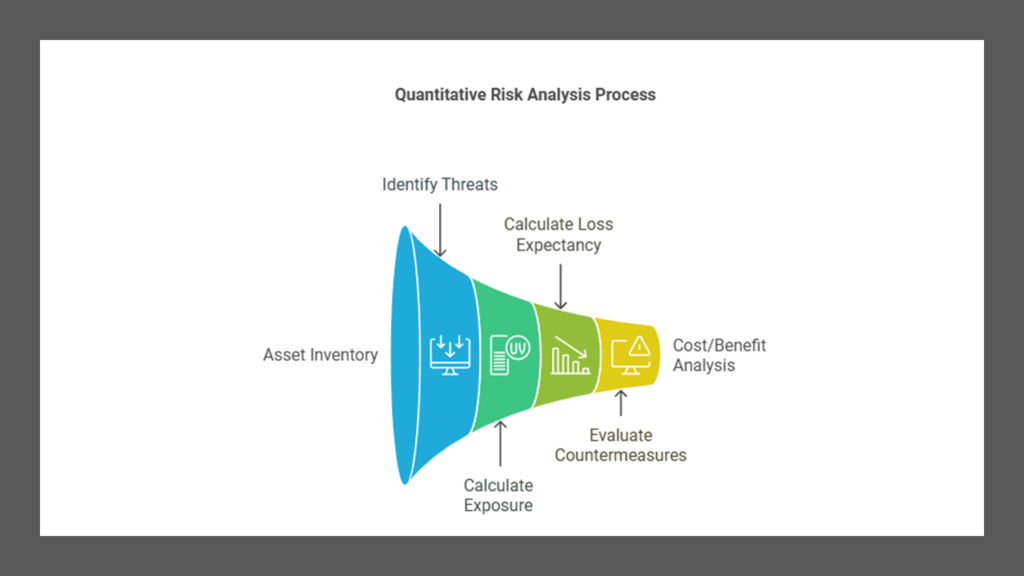
Quantitative Risk Analysis
Quantitative risk analysis assigns concrete dollar figures to potential losses and is based on mathematical calculations. The process involves several steps:
- Inventory assets and assign values (AV)
- Identify threats for each asset
- Calculate Exposure Factor (EF) for each asset-threat pair
- Calculate Single Loss Expectancy (SLE)
- Determine Annualized Rate of Occurrence (ARO)
- Calculate Annualized Loss Expectancy (ALE)
- Research and evaluate countermeasures
- Perform cost/benefit analysis
Key Formulas in Quantitative Risk Analysis:
Single Loss Expectancy (SLE):
SLE=AV×EFSLE=AV×EF
Where:
- AV is Asset Value
- EF is Exposure Factor (expressed as a percentage)
Real-world application: If a server worth $100,000 (AV) is expected to lose 25% of its value (EF) in a specific threat scenario, the SLE would be $25,000.
Annualized Loss Expectancy (ALE):
ALE=SLE×AROALE=SLE×ARO
or
ALE=AV×EF×AROALE=AV×EF×ARO
Where:
- ARO is Annualized Rate of Occurrence
Real-world application: If the SLE for a server breach is $25,000 and the ARO is 0.1 (expected to occur once every 10 years), the ALE would be $2,500.
Cost/Benefit Analysis of Safeguards:
Value of Safeguard=(ALEbefore−ALEafter)−ACSValueof Safeguard=(ALEbefore−ALEafter)−ACS
Where:
- ALE_before is the ALE before implementing the safeguard
- ALE_after is the ALE after implementing the safeguard
- ACS is the Annual Cost of the Safeguard
Real-world application: If a firewall reduces the ALE from $10,000 to $2,000 and costs $3,000 annually, its value would be $5,000 per year.
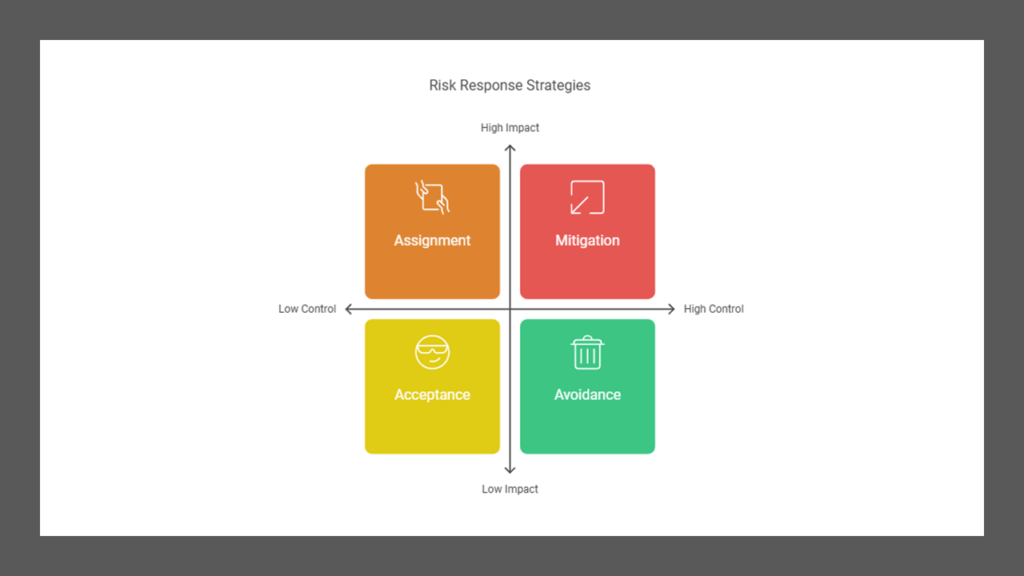
Risk Responses
Once risks are identified and assessed, management must decide how to address each risk. Possible responses include:
- Mitigation or reduction
- Assignment or transfer
- Deterrence
- Avoidance
- Acceptance
- Rejection (not recommended)
Additional Risk Management Concepts
- Inherent Risk: Default risk before any management efforts
- Residual Risk: Remaining risk after implementing safeguards
- Risk Appetite: Total amount of risk an organization is willing to accept
- Risk Capacity: Level of risk an organization can shoulder
- Risk Tolerance: Acceptable risk level for individual asset-threat pairs
Countermeasure Selection Considerations
When selecting countermeasures, consider:
- Cost vs. asset value
- Cost vs. benefit
- Effectiveness against real, identified problems
- Ability to withstand public scrutiny
- Testability and verifiability
- Consistency across users and systems
- Minimal dependencies and human intervention requirements
By understanding and applying these risk management concepts, organizations can develop effective strategies to protect their assets and support their business objectives.
Monitoring and Measurement
Security controls should provide benefits that can be continuously monitored and measured. If a security control’s benefits cannot be quantified, evaluated, or compared, then it does not actually provide any security. A security control may provide native or internal monitoring, or external monitoring may be required. This should be considered when making initial countermeasure selections.
Measuring the effectiveness of a countermeasure is not always an absolute value. Many countermeasures offer degrees of improvement rather than specific hard numbers as to the number of breaches prevented or attack attempts thwarted. Often to obtain countermeasure success or failure measurements, monitoring and recording of events both prior to and after safeguard installation are necessary. Benefits can only be accurately measured if the starting point (i.e., the normal point or initial risk level) is known.
Part of the cost/benefit equation takes countermeasure monitoring and measurement into account. Just because a security control provides some level of increased security does not necessarily mean that the benefit gained is cost-effective. A significant improvement in security should be identified to clearly justify the expense of a new countermeasure deployment.
Risk Reporting and Documentation
Risk reporting is a key task to perform at the conclusion of a risk analysis. It involves producing a risk report and presenting it to relevant parties. For many organizations, risk reporting is an internal concern only, while others may have regulations mandating third-party or public reporting of risk findings.A risk report should be:
- Accurate
- Timely
- Comprehensive of the entire organization
- Clear and precise to support decision-making
- Updated on a regular basis
There are two main types of risk reporting:
- Internal reporting: Intended for internal stakeholders like executives, management, and employees. It supports informed decision-making and risk mitigation within the organization.
- External reporting: Intended for external stakeholders like regulatory bodies, shareholders, and the public. It provides transparency about the organization’s risk profile and management practices.
Two important tools for risk documentation are:
- Risk register: A document that inventories all identified risks, evaluates their severity, prescribes responses, and tracks risk mitigation progress.
- Risk matrix or risk heat map: A visual representation of risks on a graph or chart, often comparing probability and potential damage.
Continuous Improvement
Risk analysis is not a one-time event. Threats and vulnerabilities constantly change, so risk assessments need to be redone periodically to support continuous improvement. Any implemented security solution requires updates and changes over time. If a continuous improvement path is not provided by a selected countermeasure, it should be replaced with one that offers scalable improvements to security.An enterprise risk management (ERM) program can be evaluated using the Risk Maturity Model (RMM). The typical RMM levels are:
- Ad hoc
- Preliminary
- Defined
- Integrated
- Optimized
Legacy Risk
An often-overlooked area of risk is that of legacy devices, which may be End of Life (EOL) and/or End of Support/End of Service Life (EOS/EOSL):
- End of Life (EOL): The point at which a manufacturer no longer produces a product.
- End of Service Life (EOSL) or End of Support (EOS): Systems that are no longer receiving updates and support from the vendor.
It is crucial to move off EOSL systems to maintain a secure environment. Although it might not seem initially cost-effective to replace a working solution, the security management efforts expended will likely far exceed the cost of developing and deploying a modern system-based replacement
Risk Frameworks
Risk frameworks provide guidelines for how risk is to be assessed, resolved, and monitored. Some important risk frameworks include:
- International Organization for Standardization (ISO)
- National Institute of Standards and Technology (NIST)
- Control Objectives for Information and Related Technologies (COBIT)
- Sherwood Applied Business Security Architecture (SABSA)
- Payment Card Industry (PCI)
Two notable frameworks are:
- NIST Cybersecurity Framework (CSF): Based on five core functions: Identify, Protect, Detect, Respond, and Recover. The CSF 2.0 (released in early 2024) added a sixth function: Govern.
- NIST Risk Management Framework (RMF): Defined in SP 800-37 Rev. 2, it establishes mandatory security requirements for U.S. federal agencies. It has seven phases: Prepare, Categorize, Select, Implement, Assess, Authorize, and Monitor
These frameworks provide structured approaches for organizations to assess, develop, and enhance their cybersecurity posture and resilience against cyberthreats.



